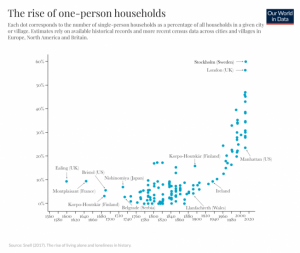
- According to Researchers, more than half of the households in Stockholm and London are occupied by just one person.
- People are more likely to live alone in rich countries around the world.
According to Researchers, Only in the U.S. The share of adults who live alone has doubled over the last 5 decades.
This is not only seen happening in the US: but it is increasingly happening all around the world including Angola to Japan.
According to Historical records which shows that the increasingly numbers on living alone just started back in early industrialized countries over a century ago, accelerating around 1950.
In states like Norway and Sweden, A single person households were very unique just a 100 years ago, but today they account for nearly half of all households, in Some cities they are already the majorities.
Have You Read?
1) Top 4 Ways to Avoid Distractions and Get Things Done
2) Top 3 Essentials For Success: Positive Thinking, Exercise, and Sleep
3) The Worst Part Of Anxiety Is Feeling Unloved, Unimportant, And Unappreciated
Social Connections: Which includes contacts with your friends and family is very essential and very important for our health and emotional well being.
Well, as a single person living alone become more common, it will bring new challenges to connect and provide support to those living alone, particularly in poorer countries where welfare states are weaker.
Evidence from Rich Countries: