Techie Talks
-
DMCA

Digital Millennium Copyright Act (DMCA)
Digital Millennium Copyright Act (DMCA): The DMCA is not often considered in a discussion of hacking and the question of…
Read More » -
Uncategorized
Session Hijacking and Web Apps
Session Hijacking and Web Apps: Session hijacking at the application level focuses on gaining access to a host by obtaining…
Read More » -
CEH Course

Ethics and The Law
Ethics and The Law: As an ethical hacker, you need to be aware of the law and how it affects…
Read More » -
Security+
Understanding Hashing
Understanding Hashing Simply yet, hashing can be considered a type of one-way encryption. Most accurately, it is a process that…
Read More » -
Black Hat
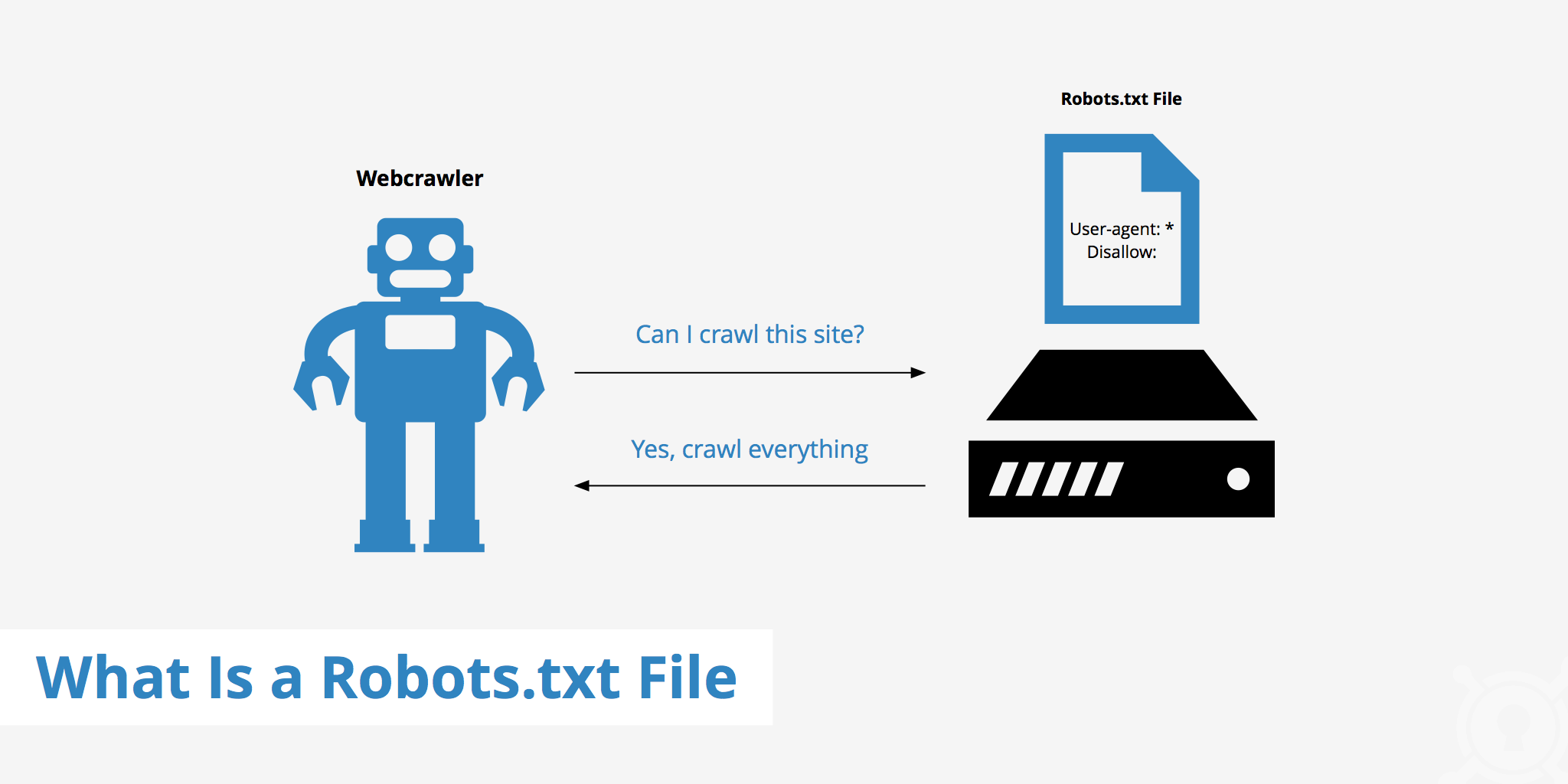
The Robots.txt File
The Robots.txt File One way to begin understanding what’s running on a web server is to view the server’s robots.txt…
Read More » -
Black Hat

JTR: KING OF THE PASSWORD CRACKERS
JTR: KING OF THE PASSWORD CRACKERS: It is hard to imagine discussing a topic like the basics of hacking without…
Read More » -
Black Hat

Password Cracking Techniques
Password-Cracking Techniques Popular culture would have us believe that cracking password is a simple as running some software and tapping…
Read More » -
CSEA

Cyber Security Enhancement Act of 2002 – CSEA
Cyber Security Enhancement Act of 2002 – CSEA Several years ago, Congress determined that the legal system still allowed for…
Read More » -
Plagiarism Checker

Plagiarism Checker X Pro – Life Time Activated Software | Best For Bloggers, Students & Teachers
Plagiarism Checker X Pro – Life Time Activated In simple words, Plagiarism Checker X Pro is software which you can…
Read More » -
Black Hat

Hunting Cross-Site Scripting (XSS)
Hunting Cross-Site Scripting (XSS) If you are not familiar with XSS attacks, make sure you read the OWASP article “Cross…
Read More »