HOW TO FIND OUT THE TOTAL NUMBER OF SIMs REGISTERED AGAINST YOUR CNIC or FOREIGN ID
HOW TO FIND OUT THE TOTAL NUMBER OF SIMs REGISTERED AGAINST YOUR CNIC?
Visit Now ( https://cnic.sims.pk/ )
To find out the total numbers of your SIMs which are registered against your CNIC, you will need to enter your CNIC number on the box below and click on the Submit button. In case of Foreign Nationals, Then you will need to select Foreign ID in the box to check foreign Identity.
Pakistani Nationality OR Foreign Nationality (You Can Check Both)
Pakistani Nationality:-
You need to select CNIC Option if you are Pak Nationality & then just type your CNIC and Press Submit. So you will be able to check whole the details.

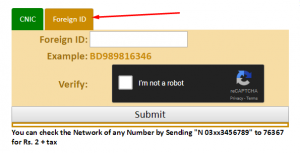
Foreign Nationality:-
If you are Foreign Nationality Person then you need to select Foreign ID so there you can provide your ID and then click to submit and the Details will get show to you for free.
ALL THE INFORMATION PROVIDED HERE IS THEREBY ONLY FOR EDUCATIONAL AND AWARENESS PURPOSES THERE IS NO MEAN TO HURT ANYONE AND USING ANY INFORMATION ILLEGALLY IS STRICTLY PROHIBITED AND ANYTHING WRONG HAPPENS I AM NOT RESPONSIBLE FOR ANY CASE.
ALL RIGHTS RESERVED TO ONLY https://cnic.sims.pk/


Nahee hora ha he
AP ko website ka link deya gaya hai waha pe ap CNIC type kar ke sare numbers dekh sakte hai jo registered hai, yeh website jo mentioned hai official website hai.