Facebook is the Home for 74 Black Market Groups
The researchers at CISCO TALOS, which has detected unusual activity of 70 Facebook groups, which were found out to be selling black market cyber fraud services.
Some of these services have been managed to remain on Facebook for around eight years or more, according to a TALOS INTELLIGENCE blog post.
Researchers have been investigating for several months to investigate the online criminal markets on Facebook, where these researchers have successfully found out 74 groups.
These Facebook group members, who offer a very wide range of services as described as “Shady (at best) and illegal (at worst) activities,” according to the research.
Well, These groups are now removes, the groups were selling and buying or trading all types of illegal services.
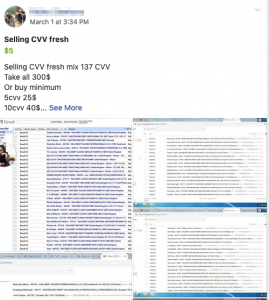
Which includes “Stolen Bank Credit Card Information, Theft of Sale of Account Credentials from a Variety of Sites, Email Spamming Tools and Services. In total, these malicious groups have around 385,000 members.”
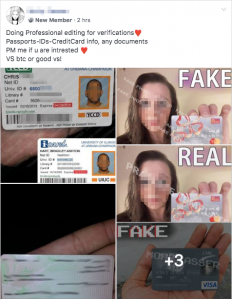
The credit cards which were often sold with their CVV numbers, as well as some of the victim’s additional identification documentation.
“Once one or more of these groups has been joined, Facebook’s own algorithms will often suggest similar groups, making new criminal hangouts even easier to find. Facebook seems to rely on users to report these groups for illegal and illicit activities to curb any abuse,” the authors wrote.
Credit: Talos Intelligence
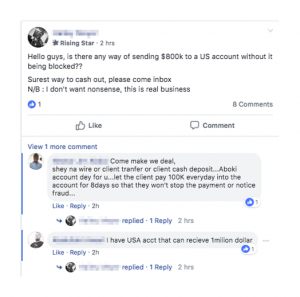
These group members who has requested government shell account or the instructions on moving a very large amount of cash, while others were offering forged identification documents.
“The majority of the time, these sellers asked for payment in the form of cryptocurrencies. Others employ the use of so-called ‘middlemen’ who act as a go-between between the buyer and the seller of the information and take a cut of the profits. These users usually promoted the use of PayPal accounts to complete the transaction,” according to the blog.
Take A Look At Some of the Malicious Services Provided By These Groups on Facebook