PTA Asks Whats-App Users to Enable Two-Factor Authentication
WhatsApp launches Two-Step Verification Security Feature for Their Users.
Your Account may be Hijacked by Someone who has your Authentication code that Whatsapp Provides to their Users.
This Feature will Make sure that the owner of the WhatsApp account that you are Demanding to log in.
All round the world such WhatsApp hijacking cases are sharp-sighted wherever a user of Whatsapp opens a malicious link and his/her WhatsApp account gets hacked.
Pakistan Telecommunication Authority:
The Pakistan Telecommunication Authority (PTA) has Expressed an Advisory for the Public that, They should Protect Their Whatsapp Account Against Hijacking.
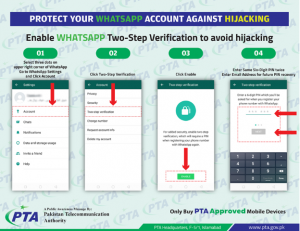
The Pakistan Telecommunication Authority (PTA) Advised the Users of WhatsApp to follow only Four Steps to protect their WhatsApp Account.
PTA Explained the Process, Four Steps that are given below in the Shap of Picture:
The Report about Hijacked WhatsApp Accounts in Many countries have compelled
their Agencies to send out Cybersecurity Alerts.
According to a recent Report by Telecom,
Hacking of Whatsapp accounts is one of the trends nowadays. In November 2018 More then 90% Whatsapp Account hacks were collected by Cyber Wing.
According to PTA, A lot of Whatsapp Accounts were hacked in Karachi, Pakistan.
The Biggest Reasons behead this Hacked is Lacking Awareness Among the Public.
Read Also: WhatsApp is Shutting down 2M accounts for Spreading Fake News
The Company of Hackers hacked the WhatsApp accounts of Large Pakistani Citizens in Karachi, Pakistan.
The Media Cited that, The Cyber Crime wing of FIA said that many of circumstance of Accounts hacking of Whatsapp were an accident in all around the world.
I will Recommend you to make sure that you have enabled the New feature Two-Factor Authentication in your WhatsApp Account.



