2 Ways Your SIM Card Can Be Hacked [Ways To Protect Against Attackers]
You must know that your smartphone’s operating systems should needs to be regularly updated to protect yourself against attackers and vulnerabilities.
But not only that your SIM card can be a huge threat as well. Right here you will learn few ways to know how hackers can use SIM cards to gain access to devices, and also we will let you know how you can protect yourself from these types of attacks.
1) SimJacker
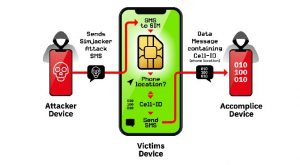
Recently Adaptive Mobile Security has announced that they have discovered a new security vulnerability, which they named “Simjacker”.
This type of attacks target SIM cards. It does this by sending a piece of spyware like code to a target device using an SMS message.
If this message gets opened, the attackers could easily spy on their calls and messages and even they can track your location.
This type of vulnerability works by using a piece of software known as S@T Browser, which a part of the SIM Application Toolkit (STK) that many phone operators use on their SIM cards.
The SIMalliance Toolbox Browser is a way of accessing the internet, in short, its a basic web browser – which lets the service providers interact with web applications like emails.
However, now a days most the devices use browsers like Google Chrome and Firefox on their device, the S@T Browser is used very less. The software is still installed on a large of devices, leaving them vulnerable to SIMJacker attack.
The security researchers believe that the exploit was developed and used by a specific private company, which is working with various government sectors to monitor any particular person. Currently, between 100 and 150 people are targeted by this attack per day.
As the attack works on SIM cards, all sort of phone devices are vulnerable, including both iPhone and Android, and even this type of attack works on embedded SIM cards (eSIMs).
2) SIM Card Swapping

Malicious attackers has various of ways to take over Twitter CEO Jack Dorsey’s personal Twitter account in August 2019. This event raised awareness of how these attacks can be destructive.
In order to person a SIM card swap, Hacker follows this:
Hacker will first call you on your phone provider. They will pretend to be you and ask for a replacement of SIM card. They will say they want to upgrade to a new device and therefore need a new SIM. if they are successful, the phone provider will send them the SIM.
Then they can easily steal your phone number and link back that to their own device.
This will have 2 different effects.
First, Your real SIM card will be deactivated by your SIM provider and will stop working.
Secondly, the attacker now has full control over phone calls, messages, and two-factor authentication requests sent to your phone number.
Which means they now these hackers have enough information to access your bank account, emails and more.
And more, even they may be able to lock you out of your other accounts.
SIM card swapping is hard to protect but not impossible. That’s because these human hackers can easily convince a customer support agent that they are you. Once they have your SIM, they have the complete control over your phone number.
How To Protect Your SIM Card?
If you are willing to protect your SIM card against malicious hackers, there are few steps you can take to protect yourself .
Protect Against Socially Engineered Attacks
To protect yourself and your SIM card swaps against hackers, you need to make it hard for hackers to find your information.
Hackers are in search to find out details about you with a search of Google/Facebook, such as names of your friend and family or your address etc.
These types of information will make it easier for hackers to easily convince the customer support agent that they are you.
Read Also : Thinking Like a Social Engineer
How To Protect Your Information on Facebook?
In order to lock down your information on Facebook, try setting your Facebook Profile to friends only and limit the public information you share on other sites. Also, do remember to delete your old accounts you no longer use to prevent them being the next target of a hack.
Read Also : Social Networking and Information Gathering
How to Protect from Phishing?
Phishing is another way of SIM card swaps, you need to be aware of phishing, Hackers are really smart they may try to phish you to get more information they can use to copy your SIM. Be on the lookout of suspicious emails or login pages, be careful where you enter your login details for any account you use.
Read Also: Phishing, Spear Phishing and Vishing
Finally, consider what methods of two factor authentication you use. Some two factor autenticaion service will send an SMS message to your device with an authenticaion code.
This means if your SIM is compromised, hackers can access your account even if you have the two factor authenticaion on.
Google Authentication App : Instead you can use another great app Google Authentication. This way the authentication is tied to your device, not your phone number, which makes it more secure against SIM card swaps.
Set a SIM Card Lock
To protect against SIM attacks you should also set up some protections on your SIM card. The most important security measure you can implement is to add a PIN code to your SIM card. This way, if anyone wants to make changes to your SIM card, they need the PIN code.
Before you set up a SIM card lock, you should ensure you know the PIN number given to you by your network provider. To set it up, on an Android device go to Settings > Lock screen and security > Other security settings > Set up SIM card lock. Then you can enable the slider for Lock SIM card.
On an iPhone, go to Settings > Cellular > SIM PIN. On an iPad, go to Settings > Mobile Data > SIM PIN. Then enter your existing PIN to confirm, and the SIM lock will be activated.
Another Security Tips [IMPORTANT]
You should use strong individually generated passwords. Remember don’t reuse old passwords or use the same password on multiple accounts.
Also, make sure your answers to password recovery questions aren’t publicly available, such as your mother’s maiden name etc.
Protect Your Device From SIM Attacks
There are protections against these types of malicious attacks, such as keeping your personal information under wraps and setting up a SIM card lock.



