
How To Add Estimated Reading Time In Your WordPress Posts
I am sure you have heard about Medium.com or you might have even visited it.
In case if you don’t know, let me tell you that it is a blogging platform which is available for public to read the stories and ideas and also you may write content on any topic that you like and publish that piece of topic to medium. It can be also very useful if you post there and you may get traffic to your site.
It displays the estimated reading time in every single post, SS attached below:

Should You Really Use Reading Time Feature on Your WordPress Website?
Think of the following:
- Checking the time left to get in touch with the support staff of any product or service
- Using GPS to check the time left to reach your destination
- Checking the total time of a video or movie
If can also encourage your users to stay on your website and read the entire article on your blog, which can be really helpful for you. And also it can reduce your Bounce Rate.
How to Display Reading Time In Your WordPress Posts
Step 1: Install the Plugin
Login to your WordPress Admin Panel, go to Plugins -> Add New.
Now search for Reading Time WP in the search box available in the top right corner. Once you find it, install and activate it:

Step 2: Setup
Once you have successfully activated the plugin, now it will do the rest, it will automatically display the reading time on your entire posts of your site. However, you can easily turn it on/off from the setting page. Also, you can make other changes as per you wish.
Let me show you how to do that:
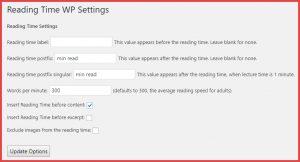
Go to Settings -> Reading Time WP from the left sidebar panel.
Here, you can easily change the text that appears before or after the time. You can also change the average reading speed which is by default 300.
You can also decide whether you may insert the reading time into your content and excerpt. Just check/uncheck the options you like and do not forget to save the changes by just clicking on the Update Options button below.
Now, let’s check out one of our posts with this feature:




2 Comments