Setting a Web Browser to Use a Proxy | Using Proxies
Using Proxies
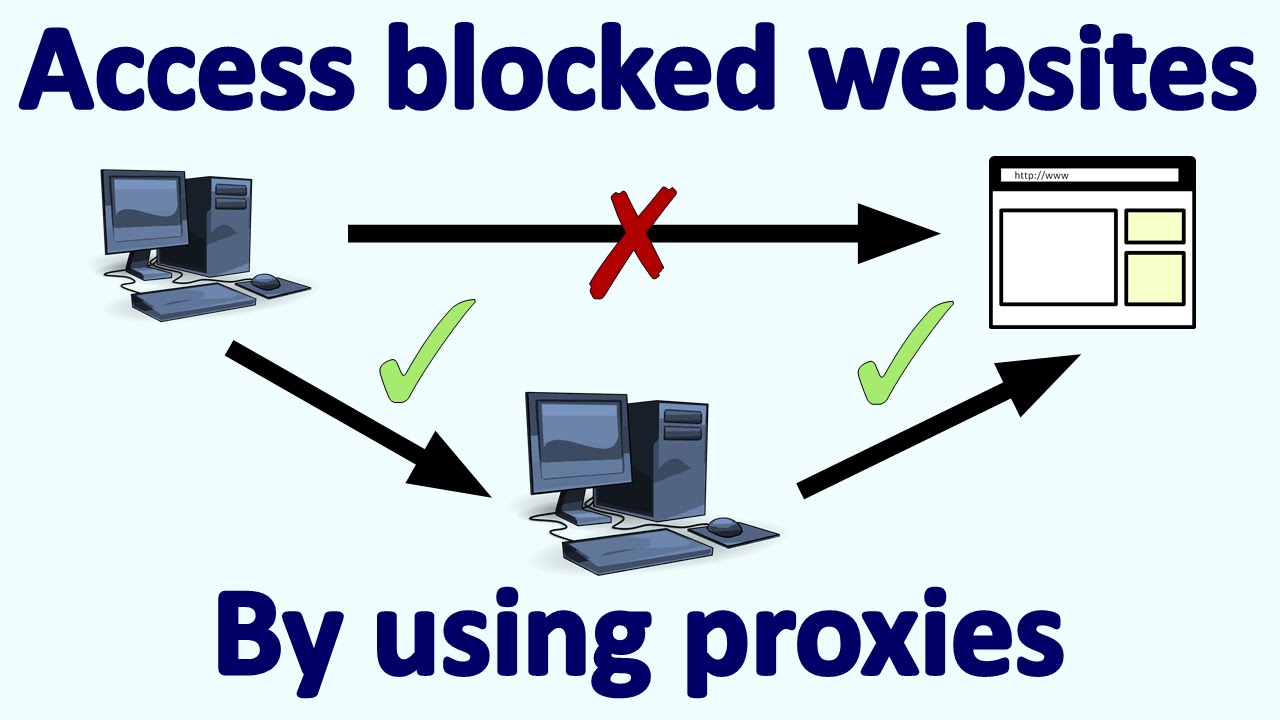
A proxy is a system acting as a stand-in between the scanner and the target. The proxy acts as an agent for the scanning party, thus providing a degree of anonymity for the scanning party. Proxy servers can perform several functions, including these:
- Filtering traffic in and out of the network.
- Anonymzing web traffic
- Providing a layer of protection between the outside world and the internal network.
Proxy servers are typically used to maintain anonymity, which helps scanners. A vigilant network administrator who checking logs and systems will see the agent or proxy but now the actual scanning party behind the proxy.
Setting up a proxy is easy and can be accomplished in a number of ways, depending on the situation.
Setting a Web Browser to Use a Proxy
Use the following steps to set your browser to use a proxy:
- Log on to whatismyip.com and write down your current IP address. Or you can use ipconfig to gain this information.
- Enter proxies in your favorite search engine to find a site providing a list of publicly available proxies. Each proxy in a list consists of an IP address and a port.
- Randomly select a proxy from the list and write down its IP address and port numbers.
- In your browser, find the proxy settings and manually configure the browser to use the information from step 3
- Check out whatismyip.com again to see how the proxy now hides your actual IP address you can configure proxies in other web browsers the same way.
Note: – Choose a proxy based outside the United States to best simulate when an advanced attacker would do. Proxies based in the United States can have their records subpoenaed, which is why a malicios party typically would refrain from using them.
Other proxy options are available to you as well that may be useful in certain situations. An important one is The Onion Router (TOR). Tor is an older technology, but it is still effective and widely used. To better understand this technology, read the following descriptions from Tor Project’s Website (http://www.torproject.org/about/overview.html.en):
Tor is a network of virtual tunnels that allows people and groups to improve their privacy and security on the internet. It also enables software developers to create new communication tools with built-in privacy features. Tor provides the foundation for a range of applications that allow organization and individuals to share information over public network without compromising their privacy.
So how does it work? Again, let’s see the developer describes the process (from the same website):
To create a private network pathway with Tor, the user’s software or client incrementally builds a circuit of encrypted connections through relays on the network. The circuit is extended one hop at a time, and each relay along the way knows only which relay gave it data and which relay it is giving data to. No individual relay ever knows the complete path that a data packet has taken. The clients negotiate a separate set of encryption keys for each hop along the circuit to ensure that each hop can’t trace these connections is they pass through.
So you can see the TOR provides you with a good amount of protection as well as the ability to obscure or encrypt traffic. Making it much more difficult to detect.
One more software product that may prove useful at hiding some or all of your presence during the information gathering process in Psiphon. This software relies on VPN technologies to hide the activity of the user from outside parties.



can you make a video how to bypaas any zip file password
sure i will.