PTA/ISP’s blocked or massively slowed down several Amazon AWS servers last night. The ones me and my team were using or impacted by were the AWS Console, Webflow and HEY email service.
AWS cloud is hosting a huge percentage of the internet, including Netflix, Apple iCloud (the last I read), Spotify, Twitter, Webflow and many other services we use daily.
Upon inquiry, I found out (first-hand information) that they were blocking traffic from these services because PUBG Mobile servers also use AWS. What kind of retards did we give keys to the Pakistani internet?
I am getting my VPN registered now because VPN’s are also blocked and I don’t know what other kinds of blunders they’re going to make. And apparently you need static-IP VPN’s and Nord/ExpressVPN/TunnelBear won’t work either.
Also Read: PTA Has Blocked Over 800,000 Websites Due to Objectionable Content in 2 Years
This VPN registration facility is only available to registered companies, so goodbye freelancers. And you need static IP for it, goodbye work-from-home employees of companies and remote workers for foreign companies.

So much for promoting IT industry in Pakistan. No foreign tech company will invest in this country. SECP already harasses VC funds coming to Pakistani startups.
People like me bring foreign currency to Pakistan. Time to consider leaving this country.
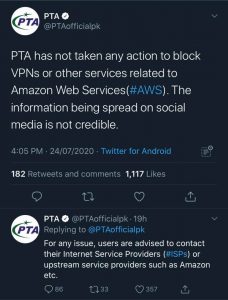
A Followup on Above Post Regarding PTA Disrupting Several AWS Services:
PTA gave a clarification statement. I would give the same statement if I worked at PTA. PTA, or some ISP’s on their behalf accidentally blocked extra AWS IP’s by trying to ban some IP addresses linked to PUBG servers. It was mostly fixed but very irresponsible and alarming because it has serious consequences on so many people’s livelihoods.
People like us from IT/ICT, including web and app developers, designers, bloggers, audio engineers, youtubers, never asked for any government subsidy, or resources like extra gas or water supply, never asked for any industrial zones, no government investment. We didn’t have reliable power, we bought UPS. No education institute teaching our craft, we learned it on our own. Internet would go out when our providers’ UPS died after a 4+ hour power outtage, we connected to our mobile internet networks in order to complete our work.
Also Read: PTA: BIGO Live Banned in Pakistan and Issue Final Warning to TikTok
We don’t have the best internet access but we’re adjusting with what we have. Hopefully in the future something like Elon Musk’s StarLink will become operational where we can use direct satellite internet and won’t have to use Pakistani internet providers either.
Despite all of these hurdles, we remain a source of a big chunk of export revenue for the country. All we needed was some easy way to get paid from our clients abroad – the only legal way to do that is still just bank transfer. Yet, they encroach on what we little space that we have.
I would relate that to how someone would make changes to a live production server and bring their client’s website down. Now imagine this happening on the country-level internet. The same thing happened when they banned YouTube and ended up disrupting several Google Apps and services as well. The same people, the same cycle repeated. You have to have a better testing mechanism, or do it in small batches first if you really have to block something.
Also Read: PTA: PUBG Is Officially Banned in Pakistan
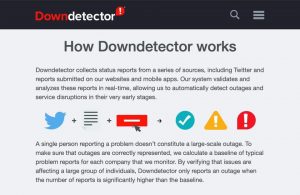
People are quoting downdetector, a region-wise monitoring tool to showcase if some service was disrupted and some people claiming that AWS was actually down. Please read how downdetector collects data. Their main data source is social media aggregation where they find data points about people complaining online or on their platform. You can make conclusions on your own.
PS: VPN block is extended to 31st July
CREDIT: Zohaib Amjad @https://web.facebook.com/zohaib.a




One Comment