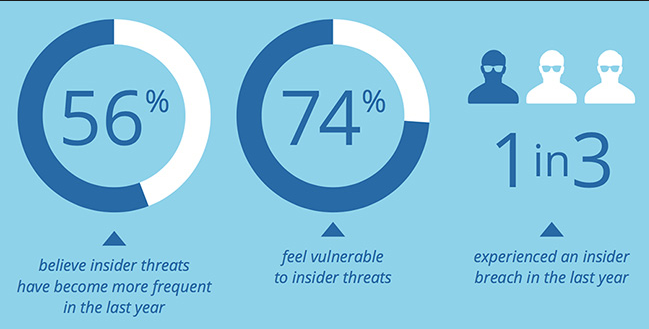
43% of Security Pros Could Execute Insider Attack
43% of Security Pros Could Execute Insider Attack: A recent survey took place of nearly 200 IT professionals about insider threats that were found nearly half of the participants who believed that they could easily attack their organizations from the inside. In a blog post earlier this week Imperva researchers who reported on insider threats and they revealed the findings of the recent survey.
179 IT professionals who participated in this survey, 43% of them said they can execute an insider attack. Only about third of them said carrying out an insider attack would be difficult or nearly impossible, while 22% who felt they had a 50/50 chance of successfully stealing the information from the inside.
When the IT professionals were asked how they could execute a successful insider attack, around 23% of which said they would use their company-owned laptop to steal the information from organization, 20% of which said they would use their personal computers, and 19% of them would use their own laptops.
“The continued reliance on data for today’s businesses means more people within an organization has access to it,” explained Imperva CTO Terry Ray. “The result is a corresponding increase in the data breaches by insiders either through intentional (stealing) or unintentional (negligent) behavior of employees and partners.”
“While the most sensational headlines typically involve infiltrating an ironclad security system or an enormous and well-funded team of insurgent, the truth of how hackers are able to penetrate your system may be less obvious; it’s your employees,” he continued.
Insider threats are continued to rank as top concerns when it comes to CyberSecurity threats, who suggested that any company could fall victim to an insider-related breach whether that could be from malicious actor or an unintended threat.
“It’s much better to put the necessary security measures in place now then to spend millions of dollars later,” Ray said. “Every company can take some basic steps in their security posture to minimize insider threats, including the background checks, monitoring employee’s behavior, using the principle of least privilege, controlling and monitoring user access, and educating the employees.”

![Bykea Had Publicly Exposed 400+ Million Users Data Including [CNIC, Address, License] ETC](https://www.techietalks.online/wp-content/uploads/2021/02/Bykea-Data-Breached.png)


One Comment