WHAT YOU NEED TO KNOW ABOUT WEB SERVERS
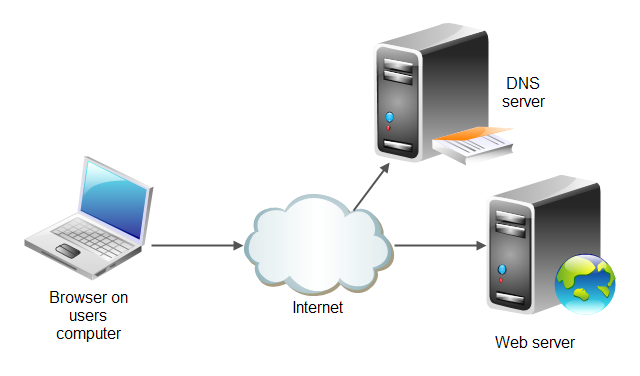
WHAT YOU NEED TO KNOW ABOUT WEB SERVERS: A web server is just a piece of software running on the operating system of a server that allows connections to access a web application.
The most common web servers are Internet Information Services (IIS) on a Windows server and Apache Hypertext Transfer Protocol (HTTP) Server on a Linux server.
These servers have normal directory structures like any other computer, and it’s these directories that house the web application.
If you follow the Windows next, next, next, finish approach to installing an IIS web server, you will end up with the default C| Inetpub | wwroot directory structure where each application will have its own directories within wwwroot and all vital web application resources are contained within it.
Linux is more varied in the file structure, but most web applications are housed in the /var/www/ directory. There are several other directories on a Linux web server that are especially relevant to web hacking:
/etc/shadow: This is where the password hashes for all users of the system
This is the “keys to the kingdom”!
/usrflib: This directory includes object files and internal binaries that are not intended to be executed by users or shell scripts. All dependency data used by the application will also reside in this directory. Although there is nothing executable here, you can really ruin somebody’s day by deleting all of the dependency files for an application.
/var/*: This directory includes the files for databases, system logs, and the
source code for web application itself!
/bin: This directory contains programs that the system needs to operate, such
as the shells, Is, grep, and other essential and important binaries. bin is short
for binary. Most standard operating system commands are located here as
separate executable binary files.
The web server is a target for attacks itself because it offers open ports and access to potentially vulnerable versions of web server software installed, vulnerable versions of other software installed, and misconfigurations of the operating system that it’s running on.
![Five Programming Languages For Software Development [2020]](https://www.techietalks.online/wp-content/uploads/2019/09/Five-Programming-Languages-For-Software-Development-2020.png)


Most intersting most usefull awesom i like it.
I comment after if i have any doubt.